

| Prev | Getting Started with Pervasive.SQL (Server edition) | Next |
Support for Active Directory Service
This section describes how to install and configure Pervasive.SQL in an environment that uses Microsoft Active Directory service.
What Is Active Directory?
Active Directory is a central component of the Windows 2000 operating system network architecture. Active Directory provides a directory service specifically designed for distributed networking environments.
The Microsoft Web site provides much information about Active Directory. The following Web links provide information to help you learn about Active Directory.
- Home page for Active Directory - http://www.microsoft.com/windows2000/technologies/directory/ad/default.asp
- Overview of Active Directory - http://www.microsoft.com/windows2000/server/evaluation/features/dirlist.asp
- Overview of Active Directory Service - http://www.microsoft.com/windows2000/server/evaluation/business/addatasheet.asp
Installation of Active Directory
Ensure that Active Directory service is installed and functioning correctly before you install Pervasive.SQL into the environment.
Microsoft provides step-by-step guides to help you install and configure Active Directory service. The following Web links provide information to help you install and manage Active Directory.
- Windows 2000 Step-by-Step Guides - http://www.microsoft.com/windows2000/techinfo/planning/walkthroughs/default.asp
- Installing a Windows 2000 Server as a Domain Controller - http://www.microsoft.com/windows2000/techinfo/planning/server/serversteps.asp
- Managing Active Directory - http://www.microsoft.com/windows2000/techinfo/planning/activedirectory/manadsteps.asp
Note that Windows 2000 implements TCP/IP as the default protocol and relies on TCP/IP for most of the services associated with the operating system, including Active Directory service. Integration of Active Directory with NetWare Directory Services is possible with Microsoft Directory Synchronization Services (MSDSS) and DirSync. For more information, refer to the Microsoft Web site: http://www.microsoft.com/WINDOWS2000/sfn/msdss.asp.
Installation of Pervasive.SQL
The installation of the Pervasive.SQL database engine in an Active Directory environment requires no special steps. Install it as described in Installing Pervasive.SQL Server .
The following environment modes are supported:
- Native mode - all domain controllers run Windows 2000
- Mixed mode - some domain controllers run Windows 2000
You may install the Pervasive.SQL database engine on a domain controller if you choose. Be aware, however, that activity on the domain controller may affect the performance of the database engine. For this reason, you may prefer to install Pervasive.SQL on a server that is not a domain controller.
Server and Client Support
Pervasive.SQL Server runs on Windows 2000 Server and Windows NT Server (version 4) within an Active Directory environment. The Pervasive.SQL clients run on all Windows 32-bit platforms within an Active Directory environment.
The DOS TCP/IP requester (BREQTCP) is supported within an Active Directory environment. The DOS SPX requester (BREQUEST or BREQNT) is not supported because it requires the SPX protocol.
Directory and File Permissions
The database engines enforce directory and file permissions set at the operating system level. An Active Directory environment does not change this behavior. For example, if you set "read only" permission on a Pervasive.SQL table file, you will be unable to write to the table.
Microsoft Terminal Services Support
Pervasive.SQL Server is supported for use with Microsoft Terminal Server and Citrix MetaFrame running within an Active Directory environment. For more information about Terminal Services and Citrix MetaFrame, see Pervasive.SQL and Terminal Services .
Pervasive Administrative Authority
Active Directory service manages the security of the network. You must grant the correct access authority at the operating system level to users who need Pervasive administrative privileges.
See Active Directory Tasks for the steps to set access authority. Users must have the following authority on the machine running the database engine:
You may grant the Log on locally authority directly to a user or to the Pervasive_Admin group (and add the user to the group).
You may create the Pervasive_Admin group on the machine running the database engine (the local machine), on the domain controller for the local machine, or on both. The database engine checks privileges first on the domain controller for the local machine then on the local machine.
An example helps illustrate this. Suppose you have two servers in your domain that run the Pervasive.SQL database engine, Server A and Server B. You could create a Pervasive_Admin group on each server and on the domain controller. You then add User 1 to the group on Server A, User 2 to the group on Server B, and User 3 to the group on the domain controller. User 1 has administrative privileges for the database engine only on Server A. Similarly, User 2 has administrative privileges only on Server B. User 3, however, has administrative privileges for the database engines on both Server A and Server B.
If you create the Pervasive_Admin group on a domain controller, then the group must be a domain local group. If you create the Pervasive_Admin group on a machine that is not a domain controller, then the Pervasive_Admin group must be a local group.
Active Directory Tasks
This section explains the tasks needed to ensure users have Pervasive administrative privileges. The tasks assume the following:
- Network user IDs have been added for users who need Pervasive administrative privileges
- A Pervasive_Admin group has been created on the domain controller and users added to the group
- Windows 2000 Server is the operating system on the domain controller.
To Create the Pervasive_Admin Group on a Domain Controller
- Click Start4Programs4Administrative Tool4Active Directory Users and Computers.
- Expand the tree for the domain to which you want to add the Pervasive_Admin group (click the plus sign).
For example, the following image shows the expanded tree for the ADSTEST.com domain.
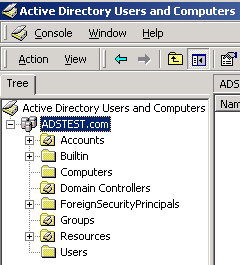
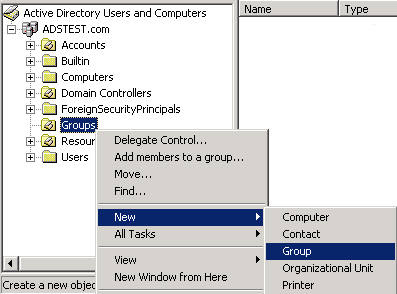
- Right-click on the Organizational Unit or folder that you are using in your Active Directory environment to house groups, then click New4Group. For example, the following image shows an Organizational Unit named "Groups," but your Organizational Unit may be named differently.
Note
If your Active Directory environment does not have an Organizational Unit to house groups, you need to create one. Click on the domain root (for example, in the figure above, you would right-click on ADSTEST.com), then click Action4New4Organizational Unit. Type a meaningful name for the unit, then click OK.
Note
The Pervasive_Admin group must have a scope of Domain local. Do not use Global or Universal.
- Click OK.
Now that the Pervasive_Admin group exists, you need to add users to it.
- On the Active Directory Users and Computers window, right-click on the Pervasive_Admin group, then click Properties. (You may also double-click the group.)
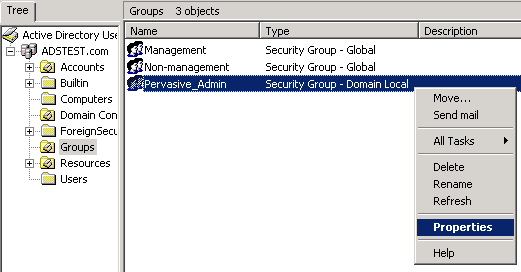
- Click the Members tab on the properties dialog.
- Click Add on the Members tab.
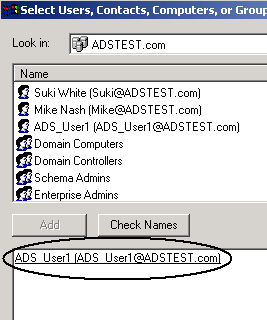
- Click on the user in the Name list that you want to add to the Pervasive_Admin group, then click Add.
The user is added to the list on the bottom. For example, the following image shows that user ADS_USER1 has been added.
- Click OK.
The user you added now appears as a member of the Pervasive_Admin group.
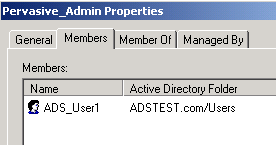
- Click OK to exit the properties dialog.
- Add the Pervasive_Admin group to the Log on locally privileges (complete the task To Grant Log On Locally Privileges to the Pervasive_Admin Group).
To Grant Log On Locally Privileges to the Pervasive_Admin Group
- Click Start4Settings4Control Panel.
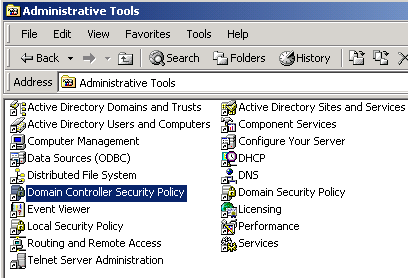
- Double-click Administrative Tools (or right-click then click Open) to open the Administrative Tools window.
- Double-click Domain Controller Security Policy (or right-click then click Open) to open the Domain Controller Security Policy window.
Note
Ensure that you open Domain Controller Security Policy and not Domain Security Policy.
- Expand the following security settings (click the plus signs):
- Click User Rights Assignment.
- Scroll the policies in the right pane until you locate Log on locally.
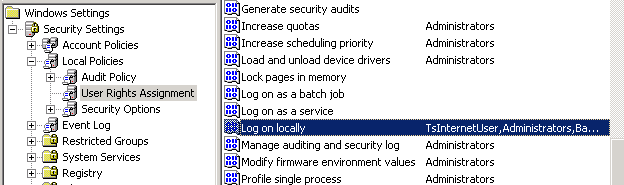
- Double-click the Log on locally policy (or right-click the policy then click Security).
The policy setting dialog appears.
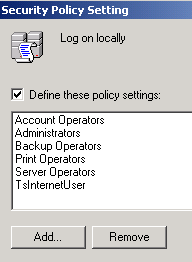
- Click Add.
- Type Pervasive_Admin in the Users and group names field.
You may also specify the group by clicking Browse and navigating to the group through dialogs.
- Click OK.
The Security Policy Setting dialog appears with Pervasive_Admin added.
- Click OK to exit the Security Policy Setting dialog.
- Exit the Domain Controller Security Policy window.
| Prev Application Configuration Scenarios |
Contents Up Check for Revisions | Next Multiple Client Applications |