

| Prev | User's Guide | Next |
Granting Administrative Rights for the Database Engine
This section begins by outlining those Pervasive.SQL V8 tasks that require administrative-level access at the operating system level and those that do not. The section then walks you through the steps to grant a user administrative-level access for each of the supported operating systems.
Note
This section only applies to the Server engine unless otherwise noted.
Tasks Requiring Administrative Rights
Administrative-level rights are required to:
- create and configure named databases and tables
- view or modify a table design with Table Designer
- set engine configuration options
- view and set engine monitoring values
- view certain engine configuration settings
How Administrative Rights are Granted
To have administrator-level access you must:
- possess full administrator-level rights on the machine on which the database engine is running (a domain administrator, for example, may lack full permissions on certain local machines), or
- be a member of the operating system group Pervasive_Admin.
To modify a table design with Table Designer, you must have full administrator rights on the machine on which the database engine is running even if you are a member of the Pervasive_Admin group.
Note
For Linux servers, administrator-level rights can be granted only by using the btadmin utility to add users and passwords to the btpasswd file.
The Pervasive_Admin option is offered so that you can grant users administrative rights to the database engine without granting them administrative rights to the operating system where the database engine resides.
Rights Within an Active Directory Environment
You may use one or more Pervasive_Admin groups within an Active Directory environment. See Support for Active Directory Service in Getting Started with Pervasive.SQL (Server edition) or Support for Active Directory Service in Getting Started with Pervasive.SQL (Workgroup edition).
Rights Provided to non-Administrative Users
Runtime-only access enables a user without administrator-level rights to perform such functions as:
- extract a list of DSNs
- extract a count of DSNs
- extract information on a DSN
- extract information on the location of the DBnames configuration file (dbnames.cfg)
- connect to databases
- retrieve, update, insert, and delete data (as permitted by database security)
Tasks for Granting Administrative Rights
To grant a user administrative rights, follow the instructions for your platform:
- Granting Administrative Rights on a Windows Server
- Granting Administrator Rights on NetWare 4.2, 5.x or 6.x
- Granting Administrator Rights on Linux
- Logging in as Administrator on any platform
Granting Administrative Rights on a Windows Server
Users who are members of Pervasive_Admin or of Administrators are permitted to perform administrative tasks on the database engine.
To grant a user database administrator rights on Windows NT
Note
You must be logged onto the Windows server as a user with full administrator-level rights on the server or be a member of the Pervasive_Admin group defined on the server.
- Open the Windows NT User Manager (click Start4Programs4Administrative Tools4User Manager.)
- Click User4New Local Group. A dialog box appears.
- Type in
Pervasive_Adminas the group name.You may now add users to this list. (Click Add, select user, click Add, click OK.)
- Click OK when finished.
Note
If the Log on as setting for the Pervasive.SQL services is not System Account, see Services Settings and Log In Authority .
To grant a user database administrator rights on Windows 2000
Note
You must be logged onto the Windows server as a user with full administrator-level rights on the server or be a member of the Pervasive_Admin group defined on the server.
- Click Start4Settings4Control Panel4Users and Passwords.
- Click the Advanced tab. In the area "Advanced User Management," click Advanced.
- Click the Groups folder. From the menu, click Action4New Group.
- Type in Pervasive_Admin as the group name.
(To add users to this group, click Add, select user name, click Add > OK.)
- Click Create to create the group.
- Click Close.
Note
If the Log on as setting for the Pervasive.SQL services is not System Account, see Services Settings and Log In Authority .
Services Settings and Log In Authority
Certain operating system settings for the Pervasive.SQL services must be in effect for you to log in to the machine running the database engine. These settings apply whether or not you use a Pervasive_Admin user group.
The settings apply to the Pervasive.SQL Server engine and to the Workgroup engine if you are running the Workgroup engine as a service. See Running the Workgroup Engine as a Service in Getting Started with Pervasive.SQL (Workgroup edition).
Default Setting
By default installation, both the Transactional and Relational services set Log on as to System Account (Local System Account on Windows 2000).
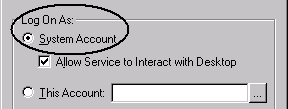
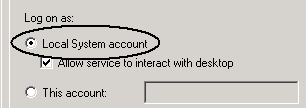
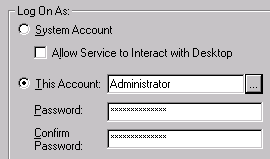
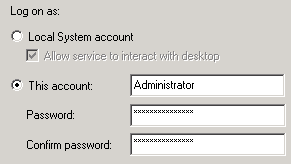
Logging On as "This Account"
If you change the Log on as setting to This account, you must change the user rights policy Act as part of the operating system for the account. Otherwise, remote login fails.
For example, both the Monitoring utility and the Configuration utility require that you log in to the operating system on the machine where the database engine is running. You will receive a message that login failed if the account specified for This account cannot act as part of the operating system.
Note that even the Administrator account requires that you set the user rights policy for Act as part of the operating system.
You specify This account on the services property sheet.
User Rights Policy Tasks
The following tasks explain how to change the user rights policy.
To Set User Rights Policy on Windows NT
- Click Start4Programs4Administrative Tools4User Manager.
- Click Policies4User Rights.
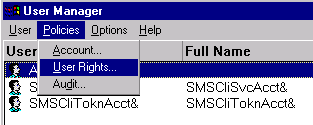
- Click the option Show Advanced User Rights.
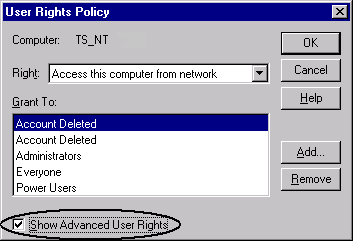
- In the Right selection list, click Act as part of the operating system.
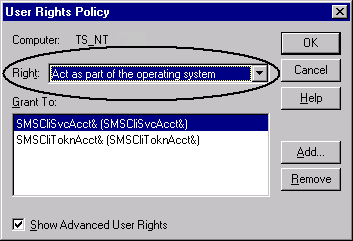
- Click Add. . .
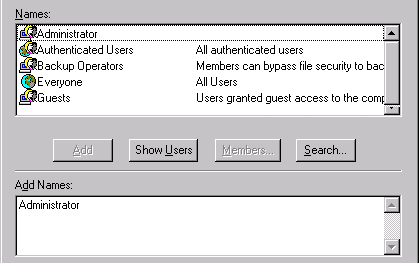
- In the Names list, click on the user or group for whose account you want to grant the user policy. (For example, you could grant the policy to the Pervasive_Admin group.)
- Click Add.
The user name is added to the Add Names list. For example, the following image shows that the Administrator has been added.
- Click OK.
The user account is added to the Grant to list.
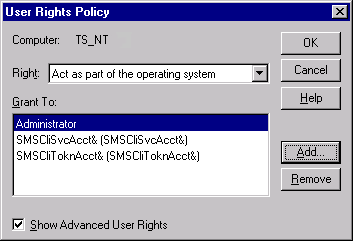
- Click OK.
- Exit User Manager.
To Set User Rights Policy on Windows 2000
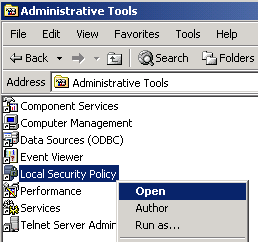
- Click Start4Settings4Control Panel.
- Double-click Administrative Tools.
- Right-click Local Security Policy, then click Open.
- Expand the tree for Local Policies (click the plus sign).
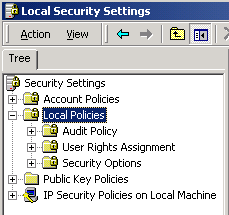
- Click on User Rights Assignment.
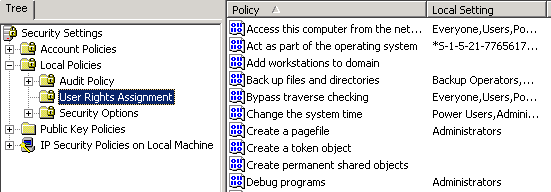
- In the policy pane, right-click Act as part of the operating system, then click Security.
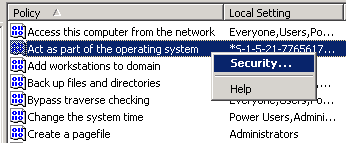
- Click Add.
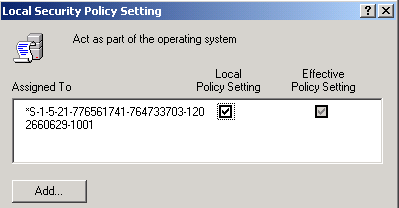
- In the Name pane, click on the user or group for whose account you want to grant the user policy. (For example, you could grant the policy to the Pervasive_Admin group.)
- Click Add.
The user name is added to the bottom pane. For example, the following image shows that the Administrator has been added.
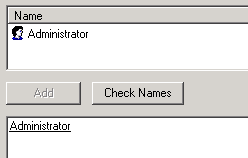
- Click OK.
The user name is added to the settings for local security policy.
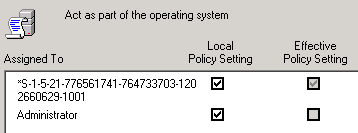
- Click OK.
- Exit the window for Local Security Settings, then exit Administrative Tools.
Granting Administrator Rights on NetWare 4.2, 5.x or 6.x
To grant a user database administrator rights on NetWare 4.2, 5.x or 6.x
- Do one of the following:
- Select the Object menu.
- Select Create. The New Object dialog box opens.
- Select Group and click OK. The Create Group dialog box opens. Enter Pervasive_Admin as the name of the group, and click Create.
- Once Pervasive_Admin is created, you can double-click on the name, and the Details dialog box for that group will appear. Members is an options page (listed in the right-hand panel of the dialog box); click on it and then click Add to select a user and click OK to close the dialog box.
Note
Users may not log in to Pervasive.SQL V8 if they are in violation of any restrictions set in their NetWare user profile. These restrictions may be accessed and changed by double-clicking the user name in the NDS tree, which will bring up the Details dialog box for that user. The Login Restrictions, Login Time Restrictions and Network Address Restrictions options pages appear in the right-hand panel of the dialog box; these may be reviewed to ensure no violations are occurring.
Granting Administrator Rights on Linux
To grant a user administrator rights on Linux
A user cannot remotely administer a server engine on Linux unless the user has first been set up as a database user with administrative rights. You can perform this task by using the btadmin utility at the server command line.
See also Pervasive.SQL Account Management on Linux in Getting Started with Pervasive.SQL (Server edition) for a complete discussion of configuring the environment for administrative rights.
- Login to the Linux server as
psql(or asrootif the PATH and LD_LIBRARY_PATH variables have been set and exported). No other user is permitted to run btadmin.- Create a new user with administrative rights by running btadmin:
btadmin -p passwd a+ user_nameFor example, if you wanted to create an administrative user "tim" with password "tim56", you would enter the following command:
btadmin -p tim56 a+ tim
Note
Users created with btadmin are not related to Linux system users. These users are known only to the database engine.
Logging in as Administrator on any platform
To connect to a remote Pervasive.SQL V8 server
- Use the Monitor or Configuration utility to connect to a remote server. Refer to the Advanced Operations Guide for a discussion of these utilities.
A dialog box appears. Enter your operating system user name and password, and click OK.
Figure 2-5 Connect to Remote Server Dialog Box
The password is encrypted before being sent over the network using a unique and pre-defined encryption key. The Pervasive.SQL V8 engine unpacks and decrypts the user name and password, and verifies access. It then returns a status code to the client indicating the success or failure of the verification.
| Prev Starting and Stopping the Database Engine |
Contents Up Check for Revisions | Next Setting Up ODBC Database Access |